ADVA has demonstrated two encryption techniques for optical data transmission to counter the threat posed by quantum computing.
“Quantum computers are very powerful tools to solve specific classes of mathematical problems,” says Jörg-Peter Elbers, senior vice president, advanced technology at ADVA. “One of these classes of problems is solving equations behind certain cryptographic schemes.”
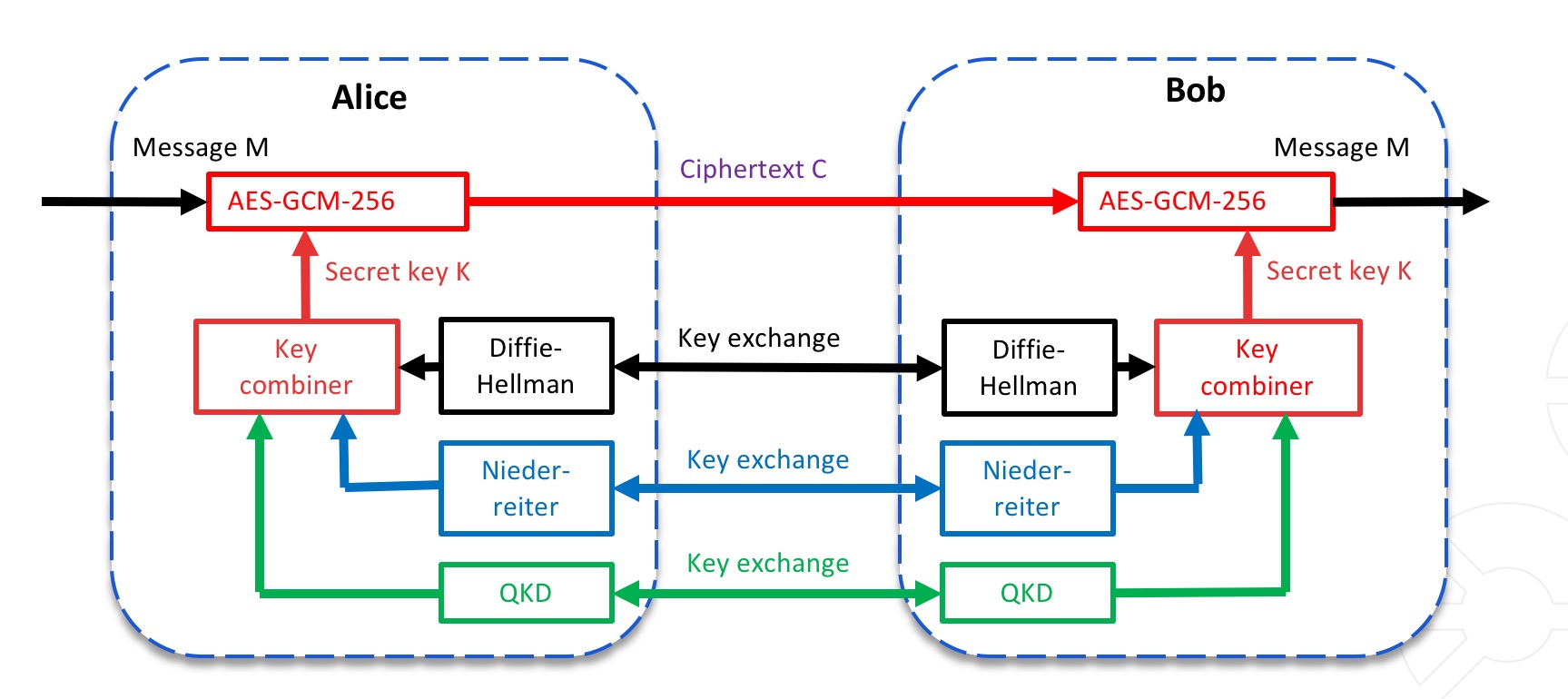 The use of three key exchange schemes over one infrastructure: classical public-key encryption using the Diffie-Hellman scheme, the quantum-resistant Neiderreiter algorithm, and a quantum-key distribution (QKD) scheme. Source: ADVA
The use of three key exchange schemes over one infrastructure: classical public-key encryption using the Diffie-Hellman scheme, the quantum-resistant Neiderreiter algorithm, and a quantum-key distribution (QKD) scheme. Source: ADVA
Public-key encryption makes use of discrete logarithms, an example of a one-way function. Such functions use mathematical operations that for a conventional computer are easy to calculate in one direction but are too challenging to invert. Solving such complex mathematical problems, however, is exactly what quantum computers excel at.
A fully-fledged quantum computer does not yet exist but the rapid progress being made in the basic technologies suggests it is only a matter of time. Once such computers exist, public key based security will be undermined.
The looming advent of quantum computers already threatens data that must remain secure for years to come. There are agencies that specialise in tapping fibre, says Elbers, while the cost of storage is such that storing huge amounts of data traffic in a data centre is affordable. “The threat scenario is certainly a real one,” says Elbers.
Demonstrations
ADVA has demonstrated two techniques, one using quantum-key distribution (QKD) and the other a quantum-resistant algorithm.
For quantum-key distribution, ADVA’s FSP 3000 platform is being used as part of the UK’s first quantum communication network that includes a metro network for Cambridge that is also linked to BT Labs in Ipswich, 120km away.
ADVA’s platform enables the exchange of keys between sites used for encoding the data traffic. In the Cambridge metro, a quantum system from Toshiba is used to encode the keys while between Cambridge and BT Labs the equipment used is from ID Quantique.
The threat scenario is certainly a real one
For ADVA’s second demonstration, a quantum-resistant encryption algorithm - one invulnerable to quantum computing attacks - is incorporated into its FSP-3000 platform to encrypt 100 gigabit-per-second traffic flows over long-haul distances. ADVA has shown secure transmissions over 2,800km, spanning three European national research and educational networks.
“There is never 100 percent security in one system but you can increase security using multiple independent systems,” says Elbers. “You can use your classical encryption methods in use today and add quantum-key distribution or a quantum-resistant algorithm or use all three over one infrastructure.” (See diagram, top.)
Quantum key distribution
Public key cryptography, comprising a public and a private key pair, is an example of an asymmetric key scheme. The public key, as implied by the name, is published with a recipient’s name. Any party wanting to send data securely to the user employs the published public key to scramble the data. Only the recipient, with the associated private key, can decode the sent data. The Diffie-Hellman algorithm is a widely used public key encryption scheme.
Jörg-Peter ElbersWith a symmetric scheme, the same key is used at both ends to lock and unlock the data. A well-known symmetric key algorithm is the Advanced Encryption Standard. AES-256, for example, uses a 256-bit key.
Although being much more efficient than asymmetrical algorithms, the issue with the symmetrical scheme is getting the secret key to the recipient without it being compromised. The key can be sent manually with armed guards. A more practical approach is to send the key over a secure link using public key cryptography; the asymmetric key exchange scheme protects the transmission of the symmetric key used for the subsequent encryption of the payload.
Quantum computing is a potent threat because it undermines all asymmetric encryption schemes in widespread use today.
Quantum key distribution, which uses particles of light or photons, is a proposed way to secure the symmetric key’s transfer. Here, single photons are used to transmit a binary signal that is then used to generate the same secret key at both ends. Should an adversary eavesdrop with a photo-detector and steal the photon, the photon will not arrive at the other end. Should the hacker be more sophisticated and try to measure the photon before sending it on, they are stymied by the laws of physics since measuring a photon changes its parameters.
Given these physical properties of photons, the sender and receiver can jointly detect a potential eavesdropper. If the number of missing or altered photons is too high, the assumption is the link is compromised.
But with quantum key distribution, the distance a photon can travel is a few tens of kilometres only. A photon is inherently low-intensity light. For longer transmission distances, intermediate trusted sites are required to regenerate the key exchange along the way. BT uses two such trusted sites on the link between Cambridge and BT Labs.
ADVA along with Toshiba have been working on an open interface that allows secure quantum key distribution over a dense wavelength division multiplexing (DWDM) link, independent of the systems used. Having an open interface also means operators using different quantum key distribution systems can interoperate and chat, says Elbers.
The US National Institute of Science and Technology (NIST) is assessing candidate quantum-resistant algorithms with the goal of standardising a suite of protocols by 2024
One way to enable single-photon streams is to use a dedicated fibre. But to avoid the expense of a separate fibre, ADVA sends the photons over a dedicated channel alongside the data transmission channels that carry much higher intensity light.
“Ideally you want a single quantum but, in practice, you might work with a highly attenuated laser source that emits less than a single quantum on average,” says Elbers. “Everything you have on your co-propagating channels can impact the performance.” ADVA uses optical filtering to ensure the data channels don’t spill over and adversely affect the key’s transfer.
Quantum-resistant algorithms
The second approach uses maths rather than fundamental physics to make data encryption invulnerable to quantum computing. The result is what is referred to as quantum-resistant techniques.
The US National Institute of Science and Technology (NIST) is assessing candidate quantum-resistant algorithms with the goal of standardising a suite of protocols by 2024.
The maths behind these schemes is complicated but what unifies them is that none are based on the mathematical problems susceptible to known quantum computing attacks.
ADVA uses the Niederreiter key exchange algorithm, one of NIST’s candidate schemes, for its system. To ensure the highest level of security for high-speed optical transmission a new symmetric key is sent frequently. The Neiderreiter algorithm uses comparatively long key lengths but Elbers points out that with a 100-gigabit payload, the overhead of long keys is minimal. Moreover, ADVA communicates key exchange information in the Optical Transport Network’s (OTN) OTU-4 frame’s overhead field.
Customers are already showing interest in quantum security, says Elbers, and is one of the reasons why ADVA is active in the UK’s Quantum Communications Hub initiative. “We are showing people that the technology is here, ready for deployment and can be integrated with existing systems,” says Elbers.
For organisations keen to ensure the long-term secrecy of their data, they need to be considering now what they should be doing to address this, he adds.